Terraform and Entra Id Authentication
Table of content
If you want to create your own or contribute to an existing GitHub project, you are on the right page.

AzureRM provider and the remote backend require authentication. The best practice is to disable storage account access key and enable Entra Id (Azure AD) authentication.
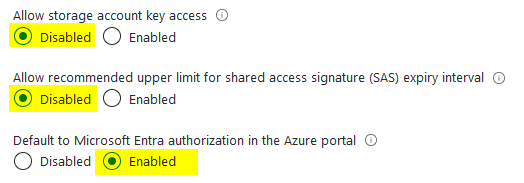
This storage account configuration will cause the following issue during the terraform init phase
1Status=403 Code="KeyBasedAuthenticationNotPermitted" Message="Key based authentication is not permitted on this storage account.
To use Entra Id authentication , here is the configuration to apply on your Terraform configuration.
On the backend.tf file, add the use_azuread_auth = true parameter.
1terraform {
2 backend "azurerm" {
3 resource_group_name = "<YOUR_BACKEND_STORAGE_RESOURCE_GROUP_NAME>"
4 storage_account_name = "<YOUR_BACKEND_STORAGE_ACCOUNT_NAME>"
5 container_name = "<YOUR_BACKEND_CONTAINER_NAME>"
6 key = "<YOUR_BACKEND_KEY_.tfstate>"
7 use_azuread_auth = true
8 }
9}
On the provider.tf file, add the storage_use_azuread = true parameter.
1terraform {
2 required_providers {
3 azurerm = {
4 source = "hashicorp/azurerm"
5 version = "4.1.0"
6 }
7 }
8}
9provider "azurerm" {
10 storage_use_azuread = true
11 skip_provider_registration = true
12 features {}
13}
If you look at the storage account activity log. The “List Storage Account Keys” operations are from before use_azuread_auth = true was enabled, and Terraform listed the keys when accessing the state file. After started using Entra ID authentication, the keys were not listed anymore.
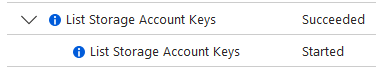
If using this access method on the Remote backend, your user or service principal needs Storage Data Blob Owner permission on the container scope.
Using Entra Id authentication for remote backend is a best practice align with RBAC and least privilege.
Please don’t hesitate to comment if there is anything wrong or inaccurate.